
Manage accessory access to Apple devices
Manage Mac computers
Accessory security (known as Restricted Mode) for macOS is designed to protect customers from close-access attacks with wired accessories. For Mac laptop computers with Apple silicon with macOS 13 or later, the default configuration is to ask the user to allow new accessories. The user has four options in System Settings for allowing accessories to connect:
Ask every time
Ask for new accessories
Automatically when unlocked
Always
If a user attaches an unknown accessory (Thunderbolt, USB or — with macOS 13.3 or later — SD Extended Capacity “SDXC” cards) to a locked Mac, they’re prompted to unlock the Mac. Approved accessories can be connected to a locked Mac for up to 3 days from when the Mac was last locked. Any accessory attached after 3 days prompts the user to “Unlock to use accessories”.
Bypassing user authorisation might be required for some environments. MDM solutions can control this behaviour by using the existing allowUSBRestrictedMode restriction to always allow accessories.
Note: These connections don’t apply to power adapters, non-Thunderbolt displays, approved hubs, paired smart cards, or to a Mac that’s in Setup Assistant or that was started from recoveryOS.
Manage iPhone and iPad devices
Managing which host computers an iPhone and iPad can pair with is important for security and user convenience. For example, the ability to securely plug into self-service stations for updating software or sharing a Mac computer’s internet connection requires a trust relationship between the iPhone or iPad and the host computer.
Device pairing is typically performed by the user when they connect their device to a host computer with a USB cable (or if an iPad model supports it, a Thunderbolt cable). A prompt appears on the user’s device asking them whether they want to establish a trust relationship with the computer.
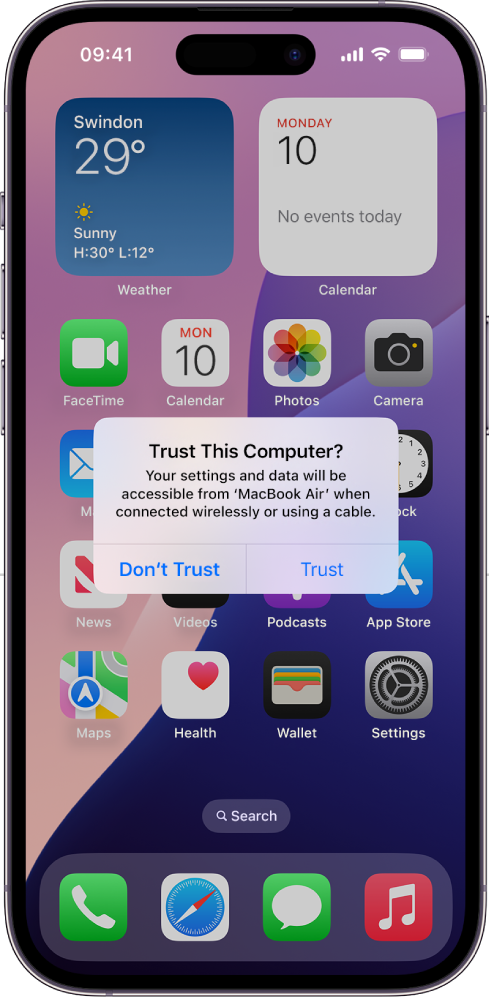
The user is then asked to enter their passcode to confirm this decision. Any further connections with the same host computer are automatically trusted going forward. Users can clear pairing trust relationships by going to Settings > General > Reset > Reset Location & Privacy, or by erasing their device. Additionally, these trust records are removed if they’re unused for 30 days.
MDM management of host pairing
An administrator can manage supervised Apple devices’ ability to manually trust host computers with the restriction Allow pairing with non-Apple Configurator hosts. By disabling the host pairing ability (and distributing the correct supervision identities to their devices), the administrator ensures that only trusted computers holding a valid supervision host certificate are allowed to access the iPhone and iPad devices in question over USB (or, if an iPad model supports it, Thunderbolt). If no supervision host certificate has been configured on the host computer, all pairing is disabled.
Note: The Apple device enrolment setting allow_pairing was deprecated with iOS 13 and iPadOS 13.1. Administrators should instead use the above guidance in the future as it provides more flexibility by still allowing pairing to trusted hosts. It also enables host pairing settings to be changed without having to erase the iPhone or iPad.
Securing unpaired restore workflows
In iOS 14.5 and iPadOS 14.5, or later, an unpaired host computer can’t restart a device into recoveryOS (also known as Recovery Mode) and restore it without local physical interaction. Before this change, an unauthorised user could erase and restore a user’s device without directly interacting with the iPhone or iPad. All they needed was a USB (or if an iPad model supports it, Thunderbolt) connection (for example, offered as a charging facility) to the target device and a computer.
Restricting external boot to recover an iPhone or iPad
By default, iOS 14.5 and iPadOS 14.5 or later, restrict this recovery capability to host computers that have been previously trusted. Administrators that want to opt out of this more secure behaviour can enable the restriction Allow putting an iOS or iPadOS device into Recovery Mode from an unpaired host.
Using Ethernet adapters with iPhone or iPad
An iPhone or iPad with a compatible Ethernet adapter maintains an active connection to a connected network even before the device is initially unlocked — if the device has the restriction turned off. This approach is useful when the device must receive an MDM command when Wi-Fi and mobile networks are unavailable, and the device hasn’t been unlocked since it was started from a shutdown state or was restarted — for example, when a user has forgotten their passcode and MDM is attempting to clear it.
The Restricted Mode setting on iPhone or iPad can be managed by:
The MDM administrator with the USB Restricted Mode restriction. This requires that the device be supervised.
The user in Settings > Touch/Face ID & Passcode > Accessories.