
Boot process for an Intel-based Mac
Intel-based Mac with an Apple T2 Security Chip
When an Intel-based Mac computer with the Apple T2 Security Chip is turned on, the chip performs a secure boot from its Boot ROM in the same fashion as iPad, iPhone, and a Mac with Apple silicon. This verifies the iBoot bootloader and is the first step in the chain of trust. iBoot checks the kernel and kernel extension code on the T2 chip, which then checks the Unified Extensible Firmware Interface (UEFI) firmware. The UEFI firmware and the associated signature are initially available only to the T2 chip.
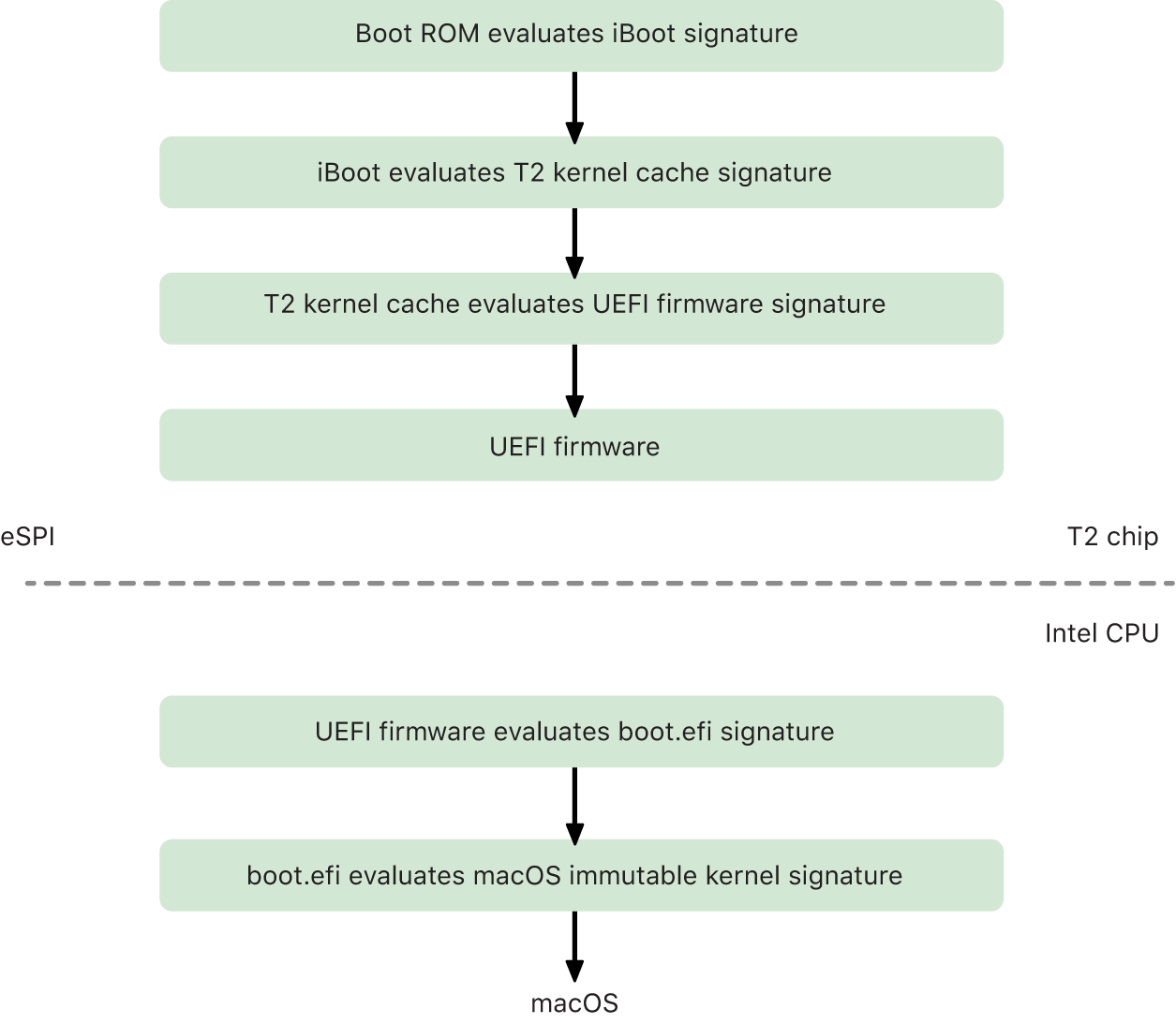
After verification, the UEFI firmware image is mapped into a portion of the T2 chip memory. This memory is made available to the Intel CPU through the enhanced Serial Peripheral Interface (eSPI). When the Intel CPU first boots, it fetches the UEFI firmware through the eSPI from the integrity-checked, memory-mapped copy of the firmware located on the T2 chip.
The evaluation of the chain of trust continues on the Intel CPU, with the UEFI firmware evaluating the signature for the macOS bootloader (Boot.efi). The Intel-resident macOS secure boot signatures are stored in the same Image4 format used for iOS, iPadOS, and T2 chip secure boot, and the code that parses the Image4 files is the same hardened code from the current iOS and iPadOS secure boot implementation. Boot.efi in turn verifies the signature of a new file, called immutablekernel. When secure boot is enabled, the immutablekernel file represents the complete set of Apple kernel extensions required to boot macOS. The secure boot policy terminates at the handoff to the immutablekernel, and after that, macOS security policies (such as System Integrity Protection and signed kernel extensions) take effect.
If there are any errors or failures in this process, the Mac enters Recovery mode, Apple T2 Security Chip Recovery mode, or Apple T2 Security Chip Device Firmware Upgrade (DFU) mode.
Microsoft Windows on an Intel-based Mac with a T2 chip
By default, an Intel-based Mac that supports secure boot trust only content signed by Apple. However, to improve the security of Boot Camp installations, Apple also supports secure booting for Windows. The UEFI firmware includes a copy of the Microsoft Windows Production CA 2011 certificate used to authenticate Microsoft bootloaders.
Note: There is currently no trust provided for the Microsoft Corporation UEFI CA 2011 that would allow verification of code signed by Microsoft partners. This UEFI CA is commonly used to verify the authenticity of bootloaders for other operating systems, such as Linux variants.
Support for secure boot of Windows isn’t enabled by default; instead, it’s enabled using Boot Camp Assistant (BCA). When a user runs BCA, macOS is reconfigured to trust Microsoft first-party signed code during boot. After BCA completes, if macOS fails to pass the Apple first-party trust evaluation during secure boot, the UEFI firmware attempts to evaluate the trust of the object according to UEFI secure boot formatting. If the trust evaluation succeeds, the Mac proceeds and boots Windows. If not, the Mac enters recoveryOS and informs the user of the trust evaluation failure.
Intel-based Mac computers without a T2 chip
Because an Intel-based Mac without a T2 chip doesn’t support secure boot, the UEFI firmware loads the boot.efi from the file system without verification and the booter loads the kernel (prelinked kernel) from the file system without verification. To protect the integrity of the boot chain, users should enable all of the following security mechanisms:
System Integrity Protection (SIP): Enabled by default, this protects the booter and kernel against malicious writes from within a running macOS.
FileVault: This can be enabled in two ways: by the user or by a device management service administrator. This protects against a physically present attacker using target disk mode to overwrite the booter.
Firmware Password: This can be enabled in two ways: by the user or by a device management service administrator. This helps prevent a physically present attacker from launching alternate boot modes such as recoveryOS, Single User Mode, or target disk mode from which the booter can be overwritten. This also helps prevent booting from alternate media, by which an attacker could run code to overwrite the booter.
