
Platform Single Sign-on for macOS
With Platform Single Sign-on (Platform SSO), developers can build SSO extensions that extend to the macOS login window, allowing users to synchronise local account credentials with an identity provider (IdP). The local account password is automatically kept in sync, so the cloud password and local passwords match. Users can also unlock their Mac with Touch ID and Apple Watch.
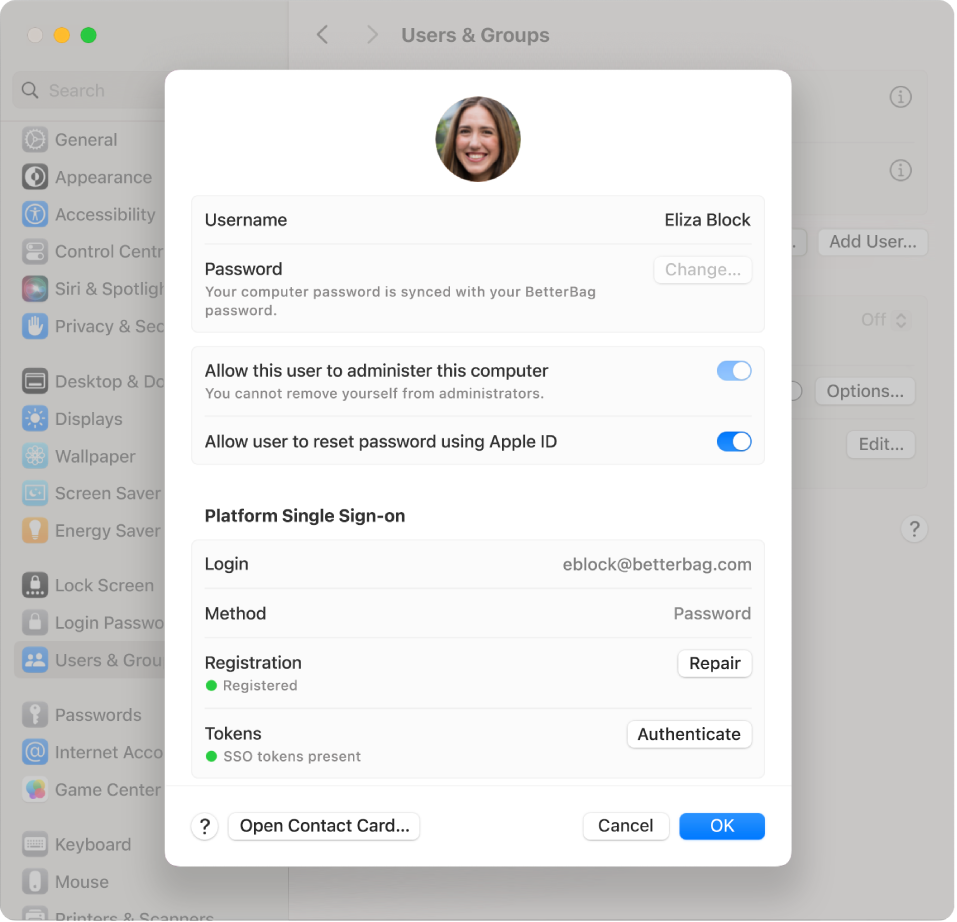
Platform SSO requires the following:
macOS 13 or later
A mobile device management (MDM) solution that supports the Extensible Single Sign-on payload which includes support for Platform SSO
Support from the IdP for the Platform SSO authentication protocol
One of two supported authentication methods:
Authentication with a Secure Enclave–backed key: With this method, a user who logs in to their Mac can use a Secure Enclave–backed key to authenticate with the IdP without a password. The Secure Enclave key is set up with the IdP during the user registration process.
Password authentication: With this method, a user authenticates with a local password or an IdP password.
Note: If the Mac is unenrolled from the MDM solution, it’s also unregistered from the IdP.
WS-Trust federation
WS-Trust federation is supported in macOS 13.3 or later. This allows Platform SSO to successfully authenticate users when their account is managed by an IdP federated with Microsoft Entra ID.
Additional Platform SSO features in macOS 14 or later
User enrolment and registration status in System Settings: Users can register their device or their user account for use with SSO in System Settings. The menu item also displays the current registration status and indicates any errors that may have occurred, providing improved user transparency. This lets the user know if the registration needs to be completed again.
Local account creation by users: To facilitate account management in shared deployments, users can use their IdP user name and password or a smart card to log into a Mac with FileVault unlocked and create a local account. The new
TokenToUserMappingkey can be used to define which attribute provided by the IdP is used to select the local user name. To use this feature, the following are required:Setup Assistant must be completed and an initial local administrator account created.
Devices must be enrolled in an MDM solution that supports bootstrap tokens.
The user’s Mac must have an Extensible Single Sign-on payload with Platform SSO and with the
UseSharedDeviceKeysandEnableCreateUserAtLoginoptions enabled.Smart card support requires that the smart card be registered with the IdP, and that there is a smart card attribute mapping configured on the Mac.
Using nonlocal IdP user accounts at authorisation prompts: Platform SSO expands the use of IdP credentials to users who don’t have a local user account on the Mac for authorisation purposes. These accounts use the same groups as Group management. For example, if the user is a member of one of the administrator groups, the account can be used at macOS administrator authorisation prompts. This excludes any authorisation prompts that require secure token, ownership permissions or authentication by the currently logged in user.
Updating group membership of users when they authenticate with their IdP: Group membership can be used to granularly manage permissions of IdP users in macOS. Every time a user authenticates with the IdP, their group membership is updated. There are three array keys available to define group membership:
AdministratorGroups: If the user is part of a group listed in this array, they will have local administrator access.
AuthorizationGroups: Specific groups used to manage built-in or custom-defined authorisation rights. The right is granted to all users who are part of the specified group. For example, membership in a group assigned to the authorisation right
system.preferences.networkallows users to modify network settings orsystem.preferences.printingallows users to modify printer settings.AdditionalGroups: Can be used by the operating system — for example, to define
sudoaccess. An entry in this array creates a group inside the local directory if the group doesn’t exist.