
Option ROM security in macOS
Note: Option ROMs aren’t currently supported on a Mac with Apple silicon.
Option ROM security in a Mac with the Apple T2 Security Chip
Both Thunderbolt and PCIe devices can have an “Option ROM (OROM)” physically attached to the device. (This is typically not a true ROM but is instead a rewritable chip that stores firmware.) On UEFI-based systems, that firmware is typically a UEFI driver which is read in by the UEFI firmware and executed. The executed code is supposed to initialise and configure the hardware it was retrieved from, so that the hardware can be made usable by the rest of the firmware. This capability is required so that specialised third-party hardware can load and operate during the earliest startup phases — for example, to start up from external RAID arrays.
However, because OROMs are generally rewritable, if an attacker overwrites the OROM of a legitimate peripheral, the attacker’s code executes early in the boot process and is able to tamper with the execution environment and violate the integrity of software that’s loaded later. Likewise, if the attacker introduces their own malicious device to the system, they’re also able to execute malicious code.
In macOS 10.12.3, the behaviour of Mac computers sold after 2011 was changed to not execute OROMs by default at the time the Mac booted unless a special key combination was pressed. This key combination protected against malicious OROMs being inadvertently introduced into the macOS boot sequence. The default behaviour of the Firmware Password Utility was also changed so that when the user set a firmware password, OROMs couldn’t execute even if the key combination was pressed. This protected against a physically present attacker intentionally introducing a malicious OROM. For users who still need to run OROMs while they have a firmware password set, a non-default option can be configured using the firmwarepasswd command-line tool in macOS.
OROM sandbox security
In macOS 10.15, UEFI firmware was updated to contain a mechanism for sandboxing OROMs and for stripping privileges from them. UEFI firmware typically executes all code, including OROMs, at the maximum CPU privilege level, called ring 0, and has a single shared virtual memory space for all code and data. Ring 0 is the privilege level where the macOS kernel runs, whereas the lower privilege level, ring 3, is where apps run. The OROM sandbox de-privileged OROMs by making use of virtual memory separation like the kernel does and then making the OROMs run in ring 3.
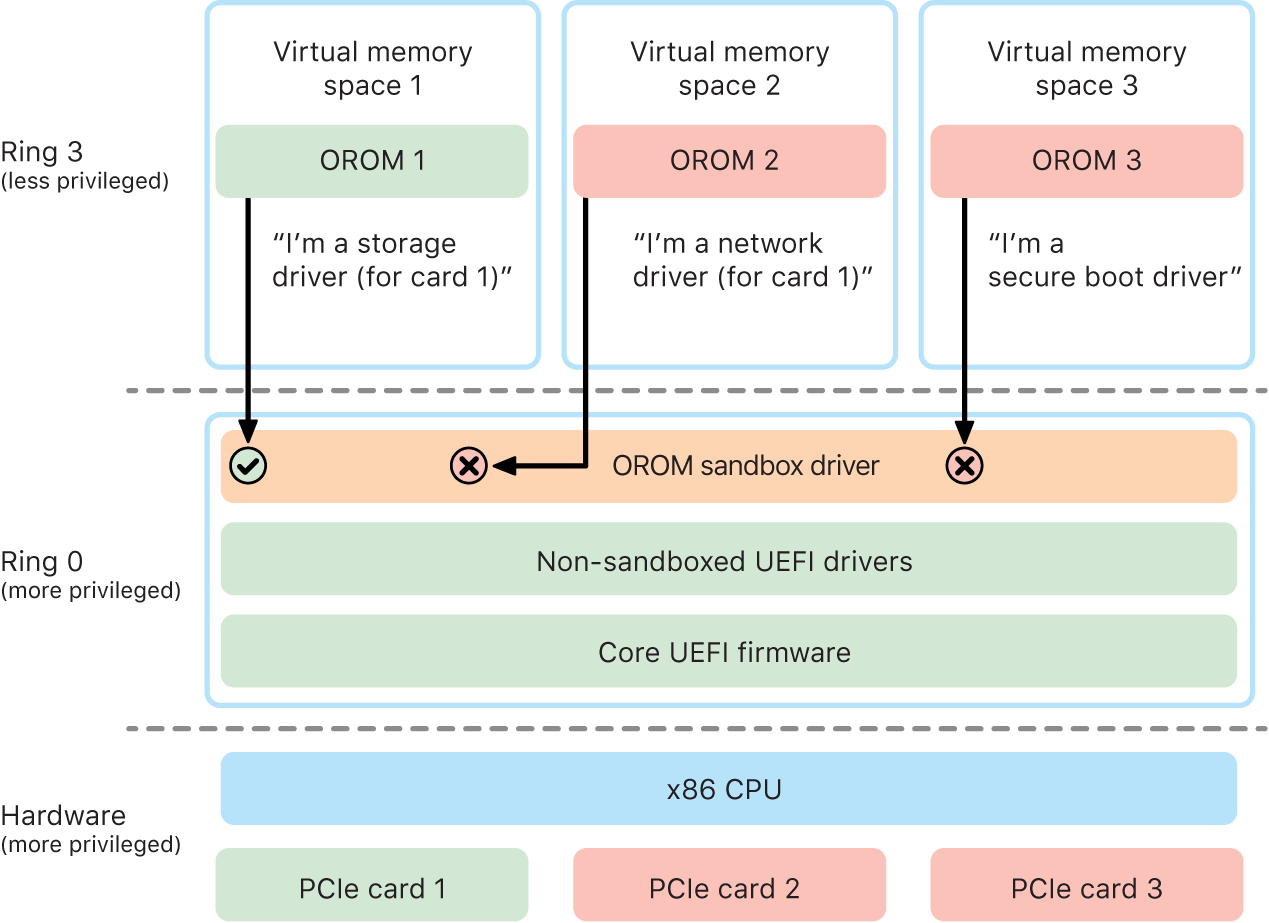
The sandbox further significantly restricts both the interfaces that the OROMs can call (much like system call filtering in kernels) and the type of device that an OROM can register as (much like app approval). The benefit of this design is that malicious OROMs can no longer directly write anywhere within ring 0 memory. Instead, they are limited to a very narrow and well-defined sandbox interface. This limited interface significantly reduces attack surface and forces attackers to first escape the sandbox and escalate privilege.