
Azure AD sync requirements with Apple Business Manager
You can use the System for Cross-domain Identity Management (SCIM) to import users into Apple Business Manager. Using this system, you merge Apple Business Manager properties (such as roles) with user account data imported from Microsoft Azure Active Directory (Azure AD). When you use SCIM to import users, the account information is added as read-only until you disconnect from SCIM. At that time, the accounts become manual accounts, and attributes in these accounts can then be edited. The initial sync takes longer to perform than subsequent cycles, which occur approximately every 40 minutes as long as the Azure AD provisioning service is running. See Provisioning tips at the Microsoft Azure documentation website.
Azure AD privileges
The following roles in Azure AD can use SCIM to sync accounts to Apple Business Manager:
Application Administrator
Cloud Application Administrator
Application Owner
Global Administrator
See Azure AD built-in roles at the Microsoft Azure AD website.
Azure AD tenants
To use SCIM with Apple Business Manager, your organisation must not have the same Azure AD tenant as any other Apple Business Manager organisation. If you want to use SCIM for your organisation, contact your Azure AD administrator to ensure that no other organisation is using your Azure AD tenant for SCIM.
Azure AD groups
In Azure AD, both sync methods use the word Groups, but only user accounts are synced. You can add Azure AD groups to the Apple Business Manager Azure AD app. For example, if you have groups in Azure AD named Engineering, Marketing and Sales, you can add those three groups to the Apple Business Manager Azure AD app. When you connect using SCIM, only accounts in those groups are synced to Apple Business Manager.
Note: Subgroups are not supported in the Apple Business Manager Azure AD app.
Provisioning scope
There are two ways you can sync accounts from Azure AD to Apple Business Manager.
Sync only assigned users and groups: this option syncs only the accounts that appear in the Apple Business Manager Azure AD app to Apple Business Manager. When using this method to sync, Azure AD accounts must have the role of user to sync to Apple Business Manager.
Sync all users and groups: this option syncs all accounts (syncing groups is not supported) that appear in the Azure AD User tab to Apple Business Manager and creates Managed Apple IDs for all federated Azure AD accounts, even if you intend to use only a specific number of accounts.
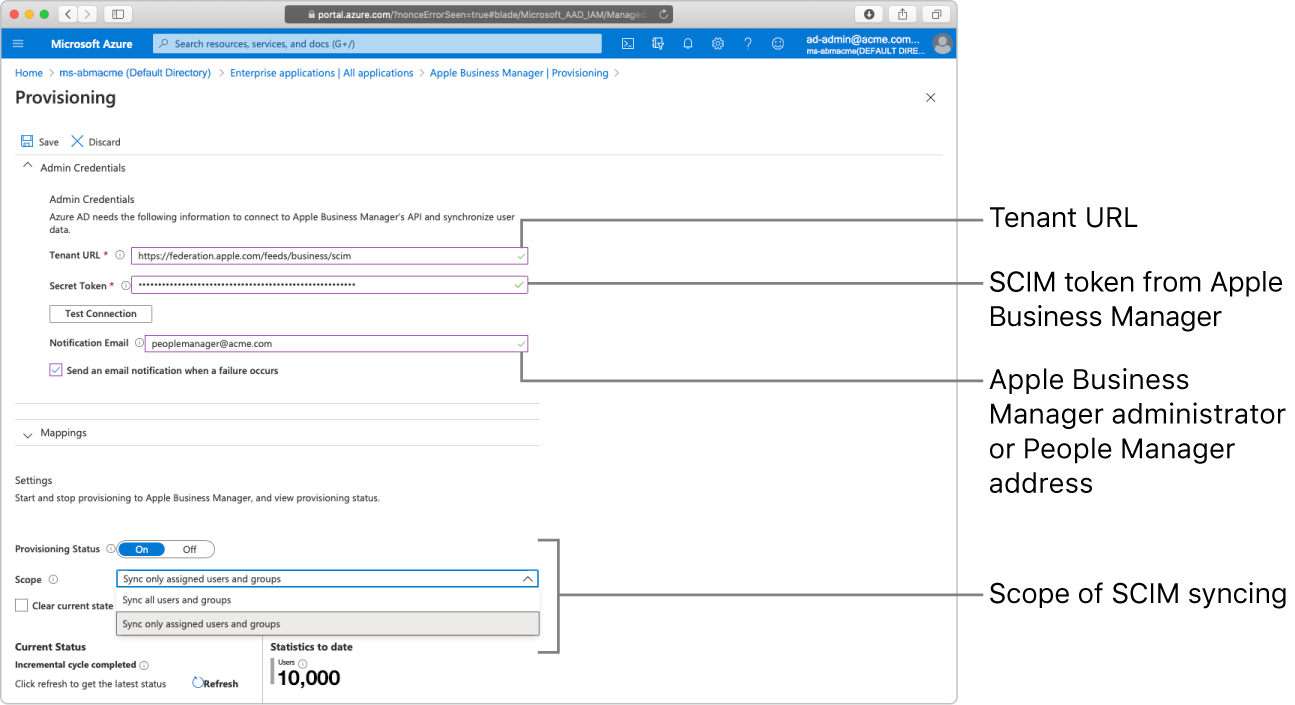
See the Microsoft Support articles What is automated SaaS app user provisioning in Azure AD? and Attribute-based application provisioning with scoping filters.
Provisioning notifications
When you configure provisioning, you should use the email address of a user that has the role of Administrator or People Manager so they can receive notifications from Azure AD.
SCIM and federated authentication
If federation is already turned on when the Azure AD accounts are sent to Apple Business Manager, you will not see an activity, but accounts will still sync from the federated domain.
Azure AD is the Identity Provider (IdP) that authenticates the user for Apple Business Manager and issues authentication tokens. Because Apple Business Manager supports Azure AD, other IdPs that connect to Azure AD like Active Directory Federated Services (ADFS) will also work. Federated authentication uses Security Assertion Markup Language (SAML) to connect Apple Business Manager to Azure AD.
Azure AD user accounts and Apple Business Manager
When a user is copied from Azure AD using SCIM to Apple Business Manager, the default role is Staff. After the sync is complete, only the Roles user attribute can be edited. This attribute is stored with the user account in Apple Business Manager and is not written back to Azure AD.
SCIM user attribute mapping
When an account is copied from Azure AD using SCIM to Apple Business Manager, the following user attributes are stored as read-only. The table also denotes whether the user attribute is required.
Important: Adding attributes not listed in the table breaks the SCIM connection.
Azure AD user attribute | Apple Business Manager user attribute | Required |
|---|---|---|
First name | First name |
|
Last name | Last name |
|
User Principal Name | Managed Apple ID and email address |
|
Object ID | (Not shown in Apple Business Manager. This attribute is used to identify conflicting accounts.) |
|
Department | Department |
|
Employee ID | Person Number |
|
Custom attribute (must be created in the Apple Business Manager Azure AD app) | Cost centre |
|
Custom attribute (must be created in the Apple Business Manager Azure AD app) | Division |
|
User Principal Name
If a user has a User Principal Name (UPN) that is exactly the same as an existing user that has the role of Administrator, no syncing is performed and the source field remains unchanged.
Person ID
When an Azure AD user is synced to Apple Business Manager, a Person ID is created for the Apple Business Manager user account. Person ID and Object ID are used to identify conflicting accounts.
If you modify the Person ID for an account previously imported from SCIM, that account is no longer paired with Azure AD. If you modified the Person ID for an account previously imported from SCIM and want to reconnect the account to SCIM, see Resolve SCIM user account conflicts.
Recommendations
You should use only the Apple Business Manager Azure AD app when connecting with SCIM.
If you have a verified domain but have not turned on federated authentication, you should wait to turn on federation until after you have verified that the Azure AD users have been sent to Apple Business Manager. Do this by viewing the Azure AD provisioning logs. After verifying that the Azure AD users have been sent, when you turn on federation, you will be notified by an activity when Azure AD users are provisioned. If federation is already turned on when the Azure AD users are sent, you will not see an activity but accounts still sync.
If you have a group configured in Azure AD, you can add that group to the Apple Business Manager Azure AD app, instead of adding each user.
Important: Do not reuse a username for 30 days in the Apple Business Manager Azure AD app.
Before you begin
Before you begin, you must do the following:
Configure and verify the domain you want to use. See Link to new domains.
Configure (but do not turn on) federated authentication. See Turn on and test federated authentication.
Note: If federated authentication is already turned on, you can still proceed. See the recommendations in the previous section.
Determine the type of syncing in Azure AD, and if necessary, create groups for syncing only assigned accounts to the Apple Business Manager Azure AD app:
Sync only assigned users.
Sync all users.
Have on call an Azure AD administrator with permissions to edit enterprise applications. When both of you are ready, see Use SCIM to import users.