How Apple protects the privacy and security of End-User Data
Apple is committed to protecting the privacy and security of End-User Data. If processed in connection with the HIPAA Covered Services, End-User Data will be stored on servers in the United States and processed in compliance with the HIPAA regulatory requirements. All End-User Data transmitted or received in connection with the HIPAA Covered Services and processed by a Customer will be governed by the Customer’s Notice of Privacy Practices and its privacy and security policies and procedures.
End-User Data that’s transmitted, stored, and otherwise processed by Apple in connection with the Health app data Share with Provider is end-to-end encrypted. Apple doesn’t store or have access to the keys used to encrypt or decrypt End-User Data. Apple processes End-User Data stored in the Health Sharing Cloud only to the extent necessary to support Health app data Share with Provider.
The diagram below shows how End-User Data is securely transmitted from the End User’s iPhone or iPad to the Customer’s EHR system.
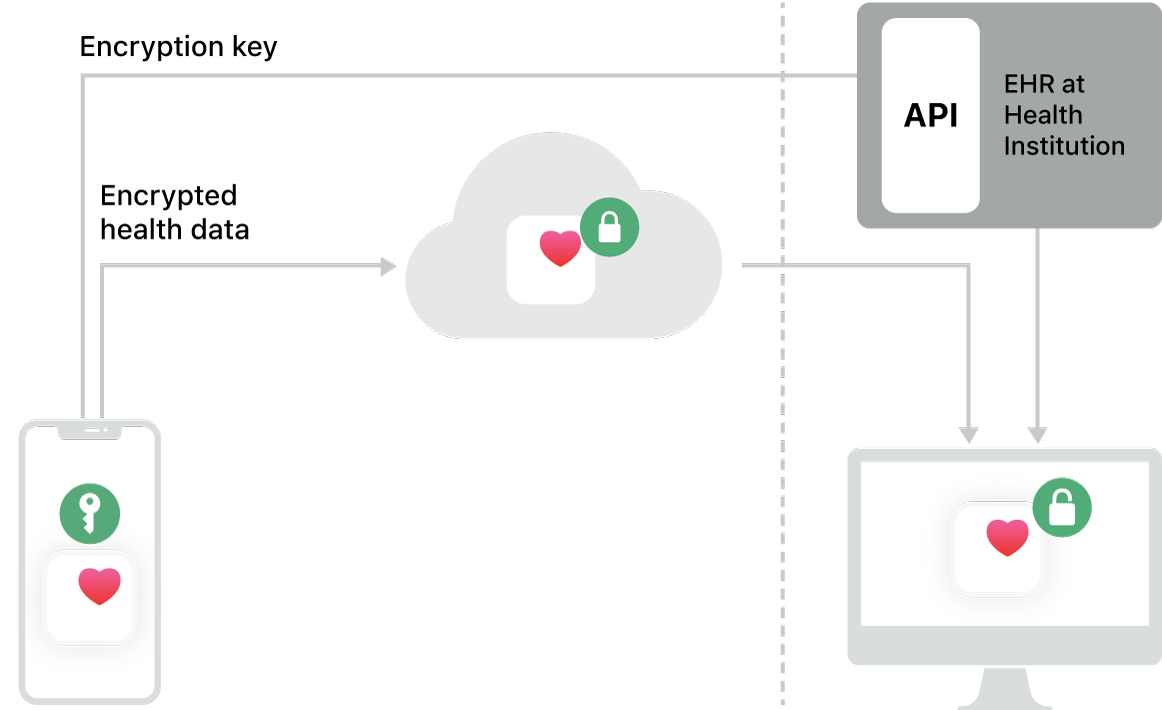
How this process works:
iPhone creates a unique symmetric Encryption Key and encrypts End-User Data using that key.
iPhone uploads the encrypted End-User Data to the Health Sharing Cloud.
iPhone uploads the Encryption Key to the EHR.
The Provider signs in to the EHR and launches the Web Application, receiving all patient context.
The Web Application retrieves the symmetric key from the EHR for the End User using the given patient context.
The Web Application retrieves the encrypted End-User Data from the Health Sharing Cloud.
Last, the Web Application decrypts the End-User Data using the symmetric key.
(The process works the same way on iPad.)
The Web Application follows best security practices to protect against security vulnerabilities, and it’s analyzed using static analysis tools to detect security risks. To protect the Web Application from potential tampering, code that’s served is validated using Subresource Integrity (SRI), a security feature that enables browsers to verify that fetched resources are delivered without unexpected manipulation. SRI allows the server to provide a cryptographic hash that a fetched resource must match. And the SMART on FHIR protocol offers protection against attempts to launch an unregistered Web Application by validating the launch_url from the Customer and the redirect_url from Apple.
Information received by Apple is treated in accordance with Appleʼs Privacy Policy, which can be found at apple.com/privacy.