Apple Platform Security
- Welcome
- Intro to Apple platform security
-
- System security overview
- Signed system volume security
- Secure software updates
- Background Security Improvements
- Operating system integrity
- BlastDoor for Messages and IDS
- Lockdown Mode security
- System security for watchOS
- Random number generation
- Communicating emergency information using satellites
- Apple Security Research Device
-
- Services security overview
-
- Apple Pay security overview
- Apple Pay component security
- How Apple Pay keeps users’ purchases protected
- Payment authorization with Apple Pay
- Paying with cards using Apple Pay
- Contactless passes in Apple Pay
- Rendering cards unusable with Apple Pay
- Apple Card security
- Apple Cash security
- Tap to Pay on iPhone
- Secure Apple Messages for Business
- FaceTime security
- Glossary
- Document revision history
- Copyright and trademarks

IPv6 security
All Apple operating systems support IPv6, implementing several mechanisms to protect the privacy of users and the stability of the networking stack. When Stateless Address Autoconfiguration (SLAAC) is used, the IPv6 addresses of all interfaces are generated in a way that helps prevent tracking devices across networks and at the same time allows for a good user experience by ensuring address stability when no network changes take place. The address generation algorithm is based on cryptographically generated addresses as of RFC 3972, enhanced by an interface-specific modifier to warrant that even different interfaces on the same network eventually have different addresses. Furthermore, temporary addresses are created with a preferred lifetime of 24 hours, and these are used by default for any new connections. The Private Wi-Fi address feature, in which unique link-local address is generated for every Wi-Fi network that a device joins, was introduced in:
iOS 14
iPadOS 14
macOS 12
visionOS 1
watchOS 7
The network’s SSID is incorporated as an additional element for the address generation, similar to the Network_ID parameter as of RFC 7217.
To protect against attacks based on IPv6 extension headers and fragmentation, Apple devices implement protection measures specified in RFC 6980, RFC 7112, and RFC 8021. Among other measures, these inhibit attacks where the upper-layer header can be found only in the second fragment (as shown below), which in turn could cause ambiguities for security controls like stateless packet filters.
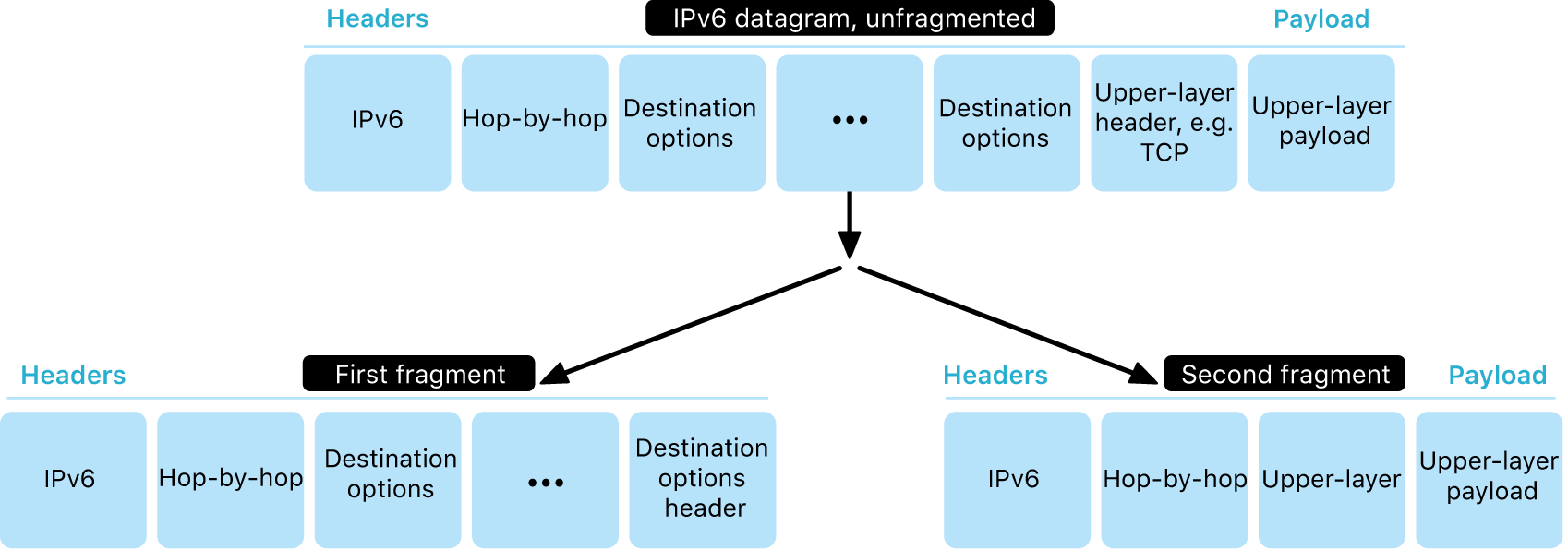
In addition, to help ensure the reliability of the IPv6 stack of Apple operating systems, Apple devices enforce various limits on IPv6-related data structures, such as the number of prefixes per interface.