
Startup Security Utility on a Mac with an Apple T2 Security Chip
On an Intel-based Mac with an Apple T2 Security Chip, Startup Security Utility handles a number of security policy settings. Users access the utility by booting into recoveryOS and choosing Startup Security Utility, and it protects supported security settings from easy manipulation by an attacker.
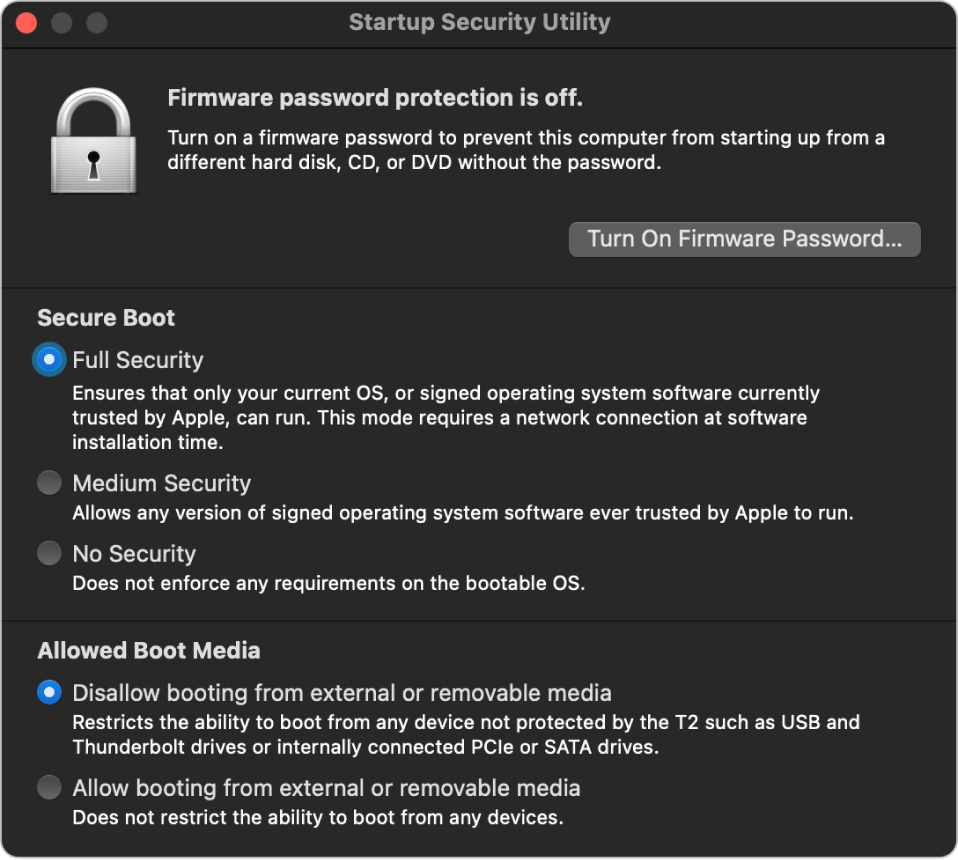
Critical policy changes require authentication, even in Recovery mode. When Startup Security Utility is first opened, it prompts the user to enter an administrator password from the primary macOS installation associated with the currently booted recoveryOS. If no administrator exists, one must be created before the policy can be changed. Before the T2 chip allows a policy change, the Mac computer needs to boot into recoveryOS and the user needs to authenticate with a Secure Enclave–backed credential. Security policy changes have two implicit requirements. recoveryOS needs to:
Boot from a storage device directly connected to the T2 chip, because partitions on other devices don’t have Secure Enclave-backed credentials bound to the internal storage device.
Reside on an APFS-based volume, because there is support only for storing the Authentication in Recovery credentials sent to the Secure Enclave on the “Preboot” APFS volume of a drive. HFS plus-formatted volumes can’t use secure boot.
This policy is shown only in Startup Security Utility on an Intel-based Mac with a T2 chip. Although most use cases shouldn’t require changes to the secure boot policy, users are ultimately in control of their device’s settings and may choose, depending on their needs, to turn off or downgrade the secure boot functionality on their Mac.
Secure boot policy changes made from within this app apply only to the evaluation of the chain of trust being verified on the Intel processor. The option “Secure boot the T2 chip” is always in effect.
Secure boot policy can be configured to one of three settings: Full Security, Medium Security, and No Security. No Security completely turns off secure boot evaluation on the Intel processor and allows the user to boot whatever they want.
Full Security boot policy
Full Security is the default boot policy, and it behaves much like iOS and iPadOS, or Full Security on a Mac with Apple silicon. At the time that software is downloaded and prepared to install, it is personalized with a signature that includes the Exclusive Chip Identification (ECID)—a unique ID specific to the T2 chip in this case—as part of the signing request. The signature given back by the signing server is then unique and usable only by that particular T2 chip. The Unified Extensible Firmware Interface (UEFI) firmware is designed to ensure that when the Full Security policy is in effect, a given signature isn’t just signed by Apple but is signed for this specific Mac, essentially tying that version of macOS to that Mac. This helps prevent rollback attacks as described for Full Security on a Mac with Apple silicon.
Medium Security boot policy
Medium Security boot policy is somewhat like a traditional UEFI secure boot, in which a vendor (here, Apple) generates a digital signature for the code to assert it came from the vendor. In this way, attackers are prevented from inserting unsigned code. We refer to this signature as a “global” signature because it can be used on any Mac, for any amount of time, for a Mac that currently has a Medium Security policy set. Neither iOS, iPadOS, nor the T2 chip itself support global signatures. This setting doesn’t attempt to prevent rollback attacks.
Media boot policy
Media boot policy exists only on an Intel-based Mac with a T2 chip and is independent from the secure boot policy. So even if a user turns off secure boot, this doesn’t change the default behavior of preventing anything other than the storage device directly connected to the T2 chip to boot the Mac. (Media boot policy isn’t required on a Mac with Apple silicon. For more information, see Startup Disk security policy control.)